Our Services
Migration Audit
The significance of data migration is often overlooked even though a lot of important business ventures and IT projects rely on its success. According to our experience the majority of the issues occurring during the change or upgrade of an information system are related to the data migration between the old and the new systems. Insufficiently regulated migration might threaten the accuracy and the integrity of the data stored in the replacement system. To ensure that the data transfer from one system to another is smooth and reliable we offer independent, comprehensive and reliable data migration audit services.

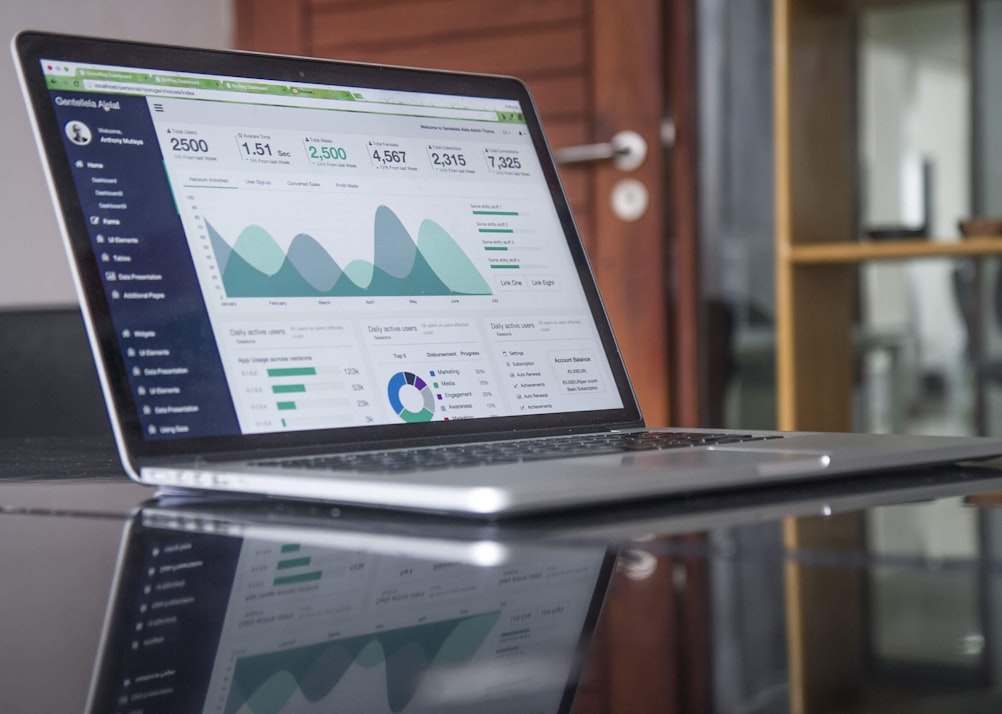
Information Technology Audit
IT Audit is the process of collecting and evaluating evidence to determine whether a computer system has been designed to maintain data integrity, safeguard assets, allows organizational goals to be achieved effectively, and uses resources efficiently. Data integrity relates to the accuracy and completeness of information as well as to its validity in accordance with the norms. An effective information system leads the organization to achieve its objectives and an efficient information system uses minimum resources in achieving the required objectives. IT Auditor must know the characteristics of users of the information system and the decision-making environment in the auditee organization while evaluating the effectiveness of any system
Gap Analysis
Gap analysis is a formal study of where an organization is currently standing regarding its Information Security vs. where it should have been or wants to be in the future. The actual performance of an organization is compared against its potential performance by collecting all the necessary information pertaining to information security and determining, documenting and approving the variance between the two. If a company or organization is not making the best use of its current resources or investment on technology, then it may be producing or performing at a level below its potential
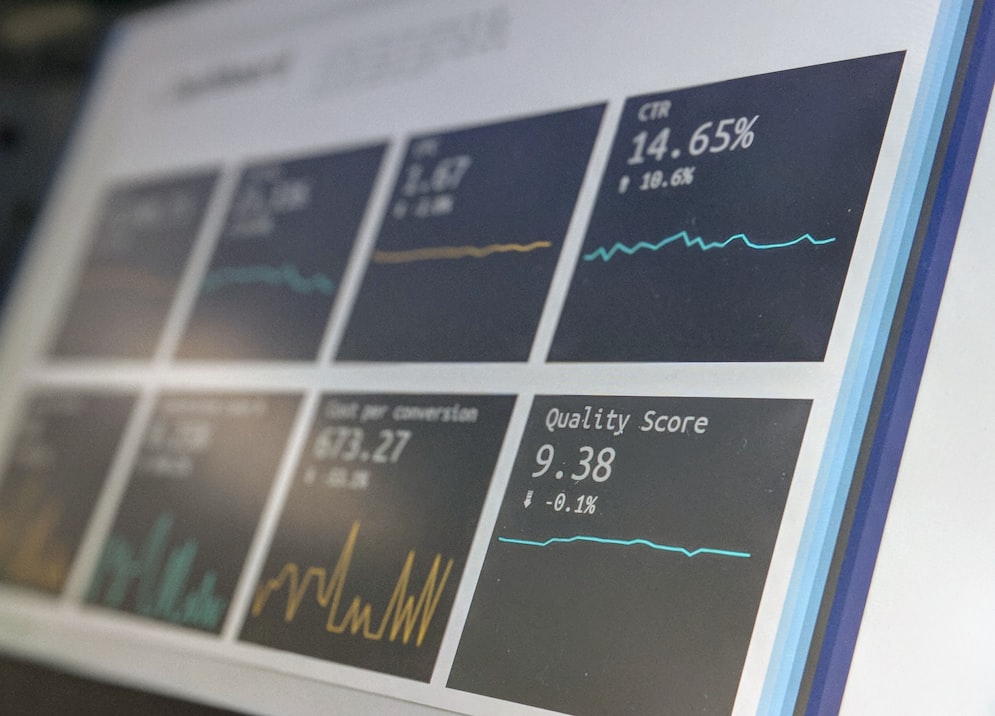

Information Security Audit
Having information security policies and procedures is not adequate for an assurance that organizational information assets are well protected. The policies may not be adequate or the compliance with the policies may not be adequate. For an assurance that they are effective in achieving their objectives a review must be performed. An Information security audit is a systematic, measurable technical assessment of how the organization’s security policy is employed. It is part of the on-going process of defining and maintaining effective security policies. Security audits provide a fair and measurable way to examine how secure a site really is. Our Advisory services offer clients a thorough, cost-effective means of evaluating their overall information Technology and Security posture in order to identify vulnerabilities and make informed remediation decisions, guided by our experience and expertise and in doing so ensure that their networks, systems, data and customers are protected from the rising tide of cybercrime.
Vulnerability Assessment
A process that determines to eliminate, mitigate or tolerate vulnerabilities based upon risk and the cost associated with fixing the vulnerability. Vulnerability management is the process surrounding vulnerability scanning, also takes into account the other aspects such as risk acceptance, remediation etc. This evaluation leads to correct the vulnerabilities and remove the risk or a formal risk acceptance by the management of an organization. A vulnerability management process should be part of an organizations' effort to control information security risks.


Penetration Testing
A penetration test is an attack on a computer system, network or a web application that has vulnerabilities which an attacker could exploit to their benefits. A penetration test is an attack on a computer system, network or web application that can have vulnerabilities which an attacker could exploit with the intention of finding personal information by potentially gaining access to the system, its functionality and the data. Penetration tests can be automated with software applications or can be done manually.
Third Party Risk Assessments
Risk Assessment helps in identifying and evaluating and controlling risks related to the organization’s objectives. With the advent of new rules and regulations internationally and adaption of new business models the need for regulatory compliance has significantly increased. Any organization small or big have to comply with these regulatory and compliance requirements nationally or internationally to comply with industry best practices and increased customer confidence. Establishing a regulatory compliance is not the end of job, rather an organization has to adapt to the continually evolving regulations and maintain them. One of the main processes of any Regulatory compliance requirement is a comprehensive Risk Assessment. Risk Assessment helps in identifying and evaluating and controlling risks related to the organization’s objectives.


Policy Development
Policy development is both the starting point and the touchstone for information security in any organization. Policies must be useable, workable and realistic while demonstrating compliance with regulatory mandates. policy audits assist the company to understand the threat of the organization .. Security auditing is a high-level analysis of the current project progress and company posture on test information security related to existing policies compliance. In addition to engaging and consulting with customers for ISO 27001. Our Solutions has also developed the policy templates to meet the IT governance needs of our client institutions.